- HUAWEI ID
- Configuring STelnet Login
- (Optional) Configuring Attributes for a VTY User Interface
- Configuring an Authentication Mode for a VTY User Interface
- Configuring a User Level for a VTY User Interface
- Configuring an SSH User
- Logging In to a Device Through STelnet
- Context
- Pre-configuration Tasks
- Configuring the Redirection Function for Device Login
- (Optional) Configuring an Authentication Mode for the TTY User Interface
- Logging In to a Device Through Redirection
- Ошибка 10016 в windows 10 и Windows Server
- Anonymous Account
- Исправление ошибки 10016 через PowerShell
- Development Process
- Configuring Login Through the Mini USB Port
- (Optional) Configuring Attributes for the Device Login Through the MiniUSB Port
- Configuring an Authentication Mode for the Mini USB Interface
- Configuring a User Level for the Mini USB Interface
- Как исправить ошибку 10016 через удаление ключей из ветки OLe
- Licensing Requirements and Limitations for CLI Login
- Involved Network Elements
- Hardware Requirements
- Узнайте больше о Huawei
HUAWEI ID
We need to use the HMS Account kit to login with Huawei ID.
Requirements For Account Kit,
– JDK 1.8 and later
– SDK Platform 26 and later
– Gradle 4.6 and later
We need to enable the account kit in our project to login with Huawei ID.
And then let’s add the account kit sdk to build.gradle in the app directory to access the methods of Account Kit from Android Studio.
Click “Sync Now” to synchronize your project.
There should be two layouts in our project. The first layout is login page, and second one is homepage. Let’s add a button to login with the Huawei ID on the login page. And let’s write the onClickListener of this button.
If you reach accessToken, it means we have finished the account kit section for this sample application. After this process, we need to transmit the accessToken AppGallery Connect.
Configuring STelnet Login
You can log in to a device using STelnet to manage and
configure the device.
The STelnet V1 protocol has security vulnerabilities.
It is recommended that you log in to the device using STelnet V2.
(Optional) Configuring Attributes for a VTY User Interface
- The system view is displayed.
- The VTY terminal service is enabled.
- If a connection remains idle for the specified timeout period, the system automatically terminates the connection after the timeout period expires, which conserves system resources.By default, the timeout period is minutes.If you set the timeout period of a terminal connection to 0 or too long, the terminal remains logged in to a device, which is a potential security risk. It is recommended that you run the command to lock the connection.
- The number of rows displayed on a terminal screen is set.The default number of rows is 24.
- Run The number of columns displayed on a terminal screen is set.The default number of columns is 80. Each character is a column.
- Run A buffer size is set for historical commands.The default buffer size is 10, that is, a maximum of 10 historical commands can be buffered.
Configuring an Authentication Mode for a VTY User Interface
- The system view is displayed.
- Run The authentication mode is set to AAA authentication.
- (Optional) Run An authentication domain is configured.
- Return to the system view.
Configuring a User Level for a VTY User Interface
- Run The system view is displayed.
Run The AAA view is displayed.
Run
Run Return to the system view. - Run The system view is displayed.
- Run The AAA view is displayed.
- Run
- Run Return to the system view.
Configuring an SSH User
- Rivest-Shamir-Adleman Algorithm (RSA) authentication: is based on the private key of the client. RSA is a public-key cryptographic system that uses an asymmetric encryption algorithm. An RSA key pair consists of a public key and a private key. You need to copy the public key generated by the client to the SSH server. The SSH server then uses the public key to encrypt data. A maximum of 20 keys can be stored on a device functioning as an SSH client.
- Elliptic Curves Cryptography (ECC) authentication: is an elliptic curve algorithm. Compared with RSA, ECC features shorter key length, lower computational cost, faster processing speed, smaller storage space, and lower bandwidth requirement under the same security performance.
A device serving as an SSH server must generate a key pair of the same type as the client’s key for data encryption and server authentication on the client. The device also supports configuration of rich SSH server attributes for flexible control on SSH login.
- The system view is displayed.
- The physical interfaces on the SSH server to which clients can connect is specified.By default, clients can connect to all the physical interfaces on the SSH server.To prevent a client from connecting to the SSH server through an unauthorized physical interface, you can run the command to specify physical interfaces on the SSH server to which the client can connect.The all parameter is supported in V300R019C11SPC100 and later versions.In V300R019C11SPC100 and later versions, this step is mandatory. If you do not perform this step, the SSH service cannot be enabled.
- Run stelnet server enableThe SSH server function is enabled on the device.By default, the SSH server function is disabled.
- An encryption algorithm list is configured for the SSH server.The server and client negotiate the algorithm for encrypting packets transmitted between them. You can run the ssh server cipher command to configure the encryption algorithm list of the SSH server. The server compares the encryption algorithm list sent from the client with its own encryption algorithm list, and selects the first matched encryption algorithm for encrypting transmitted packets. If the encryption algorithm lists of the server and client have no common encryption algorithm, the encryption algorithm negotiation fails.Only V300R019C11 version does not support the and parameters.
- A check algorithm list is configured for the SSH server.By default, an SSH server supports the algorithms only.The server and client negotiate the algorithm for checking packets transmitted between them. You can run the ssh server hmac command to configure the check algorithm list of the SSH server. The server compares the check algorithm list sent from the client with its own check algorithm list, and selects the first matched check algorithm for checking transmitted packets. If the check algorithm lists of the server and client have no common check algorithm, the check algorithm negotiation fails.Only V300R019C11 version does not support the , , , and parameters.
- A key exchange algorithm list is configured for the SSH server.By default, an SSH server supports dh_group_exchange_sha1 and dh_group1_sha1 key exchange algorithms.V300R019C10 and later versions:By default, an SSH server supports dh_group_exchange_sha1, dh_group14_sha1, and dh_group14_sha256 key exchange algorithms.V300R019C11SPC100 and later versions:By default, an SSH server supports dh_group_exchange_sha1, dh_group14_sha1, dh_group14_sha256, and dh_group15_sha512 key exchange algorithms.During the negotiation process, the client and server negotiate the key exchange algorithm for packet transmission. You can perform this step to configure a key exchange algorithm list for the SSH server. The server compares the key exchange algorithm list sent by the client with its own key exchange algorithm list, and selects the first key exchange algorithm on the client’s list that matches a key exchange algorithm on its own list as the key exchange algorithm for packet transmission. If no algorithm on the client’s list matches an algorithm on the server’s list, the negotiation fails.You are advised not to add the algorithm to the key exchange algorithm list of the SSH server because it provides low security.V300R019C10 and later versions support the dh_group14_sha1 and dh_group14_sha256 parameters.Only V300R019C11 version does not support the dh_group1_sha1 parameters.V300R019C11SPC100 and later versions support the dh_group15_sha512 parameters.
- Run rsa local-key-pair create or ecc local-key-pair createA local RSA key pair is generated.A longer key pair indicates higher security. It is recommended that you use the maximum key pair length.
- (Optional) Run ssh server port The port number of the SSH server is specified.By default, the port number of the SSH server is 22.Configuring a port number for an SSH server can prevent attackers from accessing the SSH server using the default port, improving SSH server security.
- (Optional) Run ssh server rekey-interval The interval for updating key pairs is set.The default interval is 0, indicating that the key pairs are never updated.An SSH server automatically updates key pairs at the configured intervals, which ensures security.
- (Optional) Run ssh server timeout The timeout period is set for SSH authentication.The default timeout period is 60 seconds.
- (Optional) Run ssh server authentication-retries The maximum number of SSH authentication retries is set.The default maximum number of SSH authentication retries is 3.You can set the maximum number of SSH authentication retries to prevent unauthorized access.
- (Optional) Run ssh server compatible-ssh1x enableCompatibility with earlier SSH versions is enabled.By default, compatibility with earlier SSH versions is disabled on an unconfigured device. When a device is upgraded to a later version, the configuration of the compatibility function is the same as that specified in the configuration file.If the SSH server is enabled to be compatible with earlier SSH versions, the system prompts a security risk.
- The source interface is specified for the SSH server.By default, the source interface of an SSH server is not specified.If the source IP address is not specified for the SSH server, the device selects a source IP address according to routing entries to send packets. Specify an interface in stable state, such as a loopback interface, as the source interface. Before specifying a source interface, make sure that the SSH client has a reachable route to the source interface. Otherwise, the configuration will fail.
- (Optional) Configure the function of locking IP addresses upon login authentication failure.The type of a locked object is configured.
Logging In to a Device Through STelnet
This section describes how to log in to a device using STelnet.
Context
This section describes how to use STelnet to log in to another device from the local device.
A device can function as both an STelnet server and an STelnet client. As an STelnet client, the device can log in to other devices. When a terminal lacks the necessary software or no reachable route exists between the terminal and target device, you can log in to an intermediate device and then use STelnet to log in to the target device from the intermediate device. The intermediate device functions as an STelnet client.
As shown in Figure 10-8, a PC connects to a device through network 1 and the device connects to an STelnet server through network 2. The PC cannot directly communicate with the STelnet server. In this situation, you can configure the device as an STelnet client and log in to the STelnet server from the device.
Configuring a device as an STelnet client to log in to another device
Pre-configuration Tasks
- Log in to the device from a terminal.
- Configure a reachable route between the device and STelnet server.
- Enable the STelnet server function on the STelnet server.
Configuring the Redirection Function for Device Login
After completing redirection configuration, you can log in to a remote serial port device from the local device to configure and manage the remote device.
(Optional) Configuring an Authentication Mode for the TTY User Interface
- Configure AAA authentication.The system view is displayed.
Run The authentication mode is set to AAA authentication.
The AAA view is displayed.
Exit the AAA view. - The system view is displayed.
- Run The authentication mode is set to AAA authentication.
- The AAA view is displayed.
- Exit the AAA view.
- Configure password authentication.The system view is displayed.
Run The authentication mode is set to password authentication.
Run set authentication passwordAn authentication password is set. - Run The authentication mode is set to password authentication.
- Run set authentication passwordAn authentication password is set.
Logging In to a Device Through Redirection
This section describes how to configure the redirection function and use this function to log in to a remote device.
To manage a remote device that can transmit data only through a serial port, configure the redirection function on the current device.
A remote device can be a router, a switch, an electricity terminal, a finance terminal, or other terminals that use serial ports to transmit data.
- Managing remote routers and switches Diagram for login through redirection (1)
- Managing terminals such as intelligent electricity meters, intelligent water meters, and automatic teller machinesAs shown in Figure 10-10, the redirection function is enabled on the device. The device listens to the specified TCP port and receives data packets from the terminals through serial ports. After receiving data packets, the device encapsulates the packets into Ethernet frames so that they can be transmitted over an Ethernet network. This implements the remote data transmission and management on the terminals. Diagram for login through redirection (2)
Run the display tcp status command to check the current TCP connection status.
Ошибка 10016 в windows 10 и Windows Server
На сервере Windows Server 2012 R2 постоянно возникает ошибка 10016.
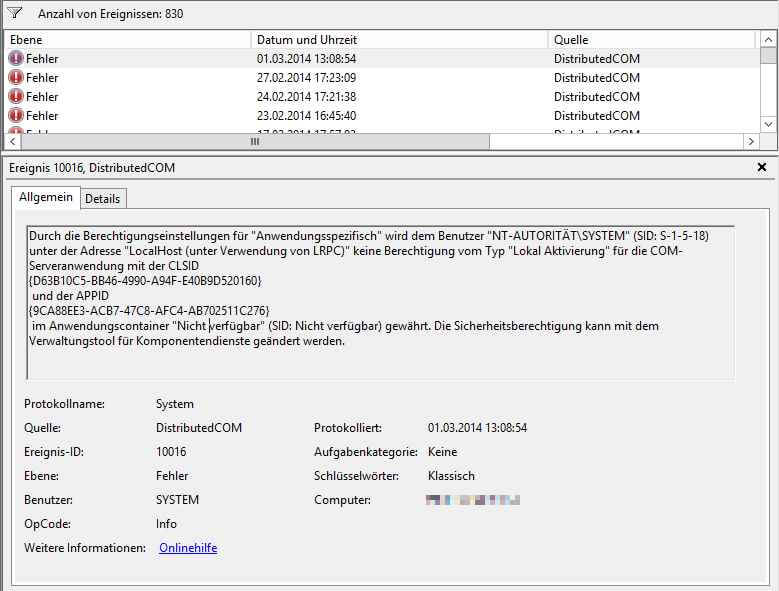
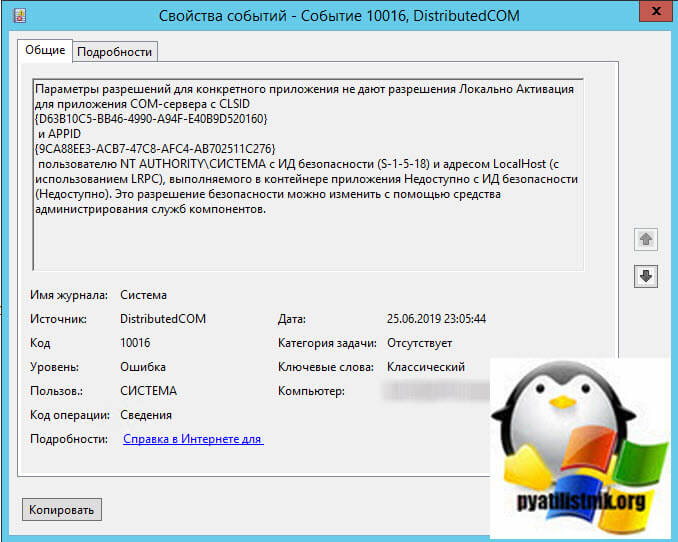
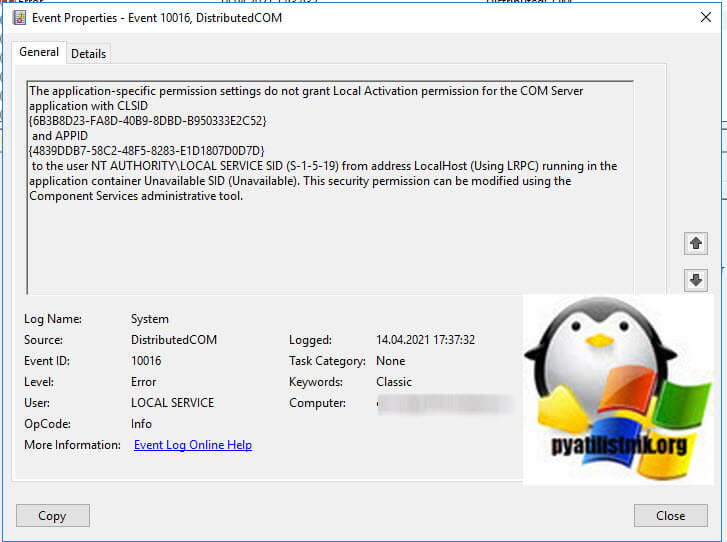
Данная ошибка выскакивает, когда какая-то из утилит не может обратиться к DCOM объекту, чаще всего, это связано с недостаточностью разрешений. Был реализован шаблон кодирования, где код сначала пытается получить доступ к компонентам DCOM с одним набором параметров. Если первая попытка не удалась, она пытается снова с другим набором параметров. Причина, по которой он не пропускает первую попытку, заключается в том, что существуют сценарии, в которых он может быть успешным. В этих сценариях это предпочтительнее. Если вы не в курсе, что такое COM объекты и DCOM, то если по простому, это концепция для создания программного обеспечения на основе взаимодействующих компонентов объекта, каждый из которых может использоваться во многих программах одновременно. На основе COM были созданы ActiveX, DCOM, COM+, DirectX, .Net.
Подробнее вы можете почитать в вики https://ru.wikipedia.org/wiki/Component_Object_Model
Сначала нужно обновить Windows через центр обновления, и если не поможет, то делаем по очереди предложенные решения:
- Удаление некоторых ключей реестра
- Использование скрипта PowerShell
Anonymous Account
We use the AGConnectAuth class for authentication. To log in as anonymous, we use the singInAnonymously () method here and add successListener and FailureListener to listen to the results. If the authentication process is successful, we are directed to HomePage.
I hope this article was useful.
You can find the sample project from github.
Finally, you can ask the problems that you encountered from the Huawei Developer forum page and see the questions that were answered previously.
Исправление ошибки 10016 через PowerShell
Или во тут
Скачиваем тут сценарий DCOMPermissions.psm1
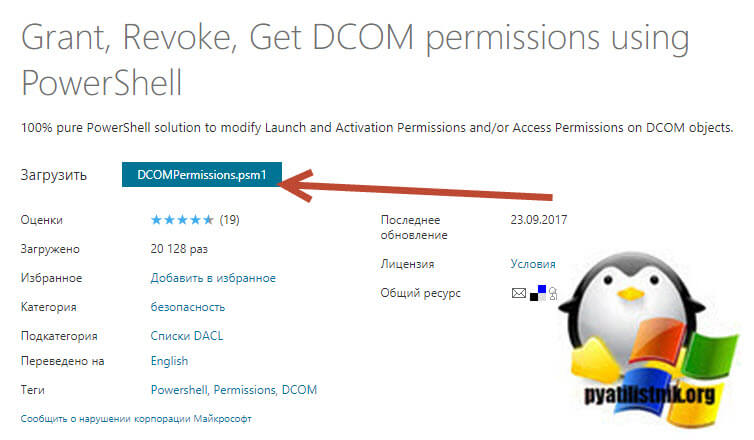
Кладем данный модуль в нужную вам папку. Далее вы открываете консоль PowerShell и переходите в месторасположение данного модуля, после чего его нужно импортировать:
Если ошибок не вышло, то значит все успешно применено, перезагрузка не потребуется.
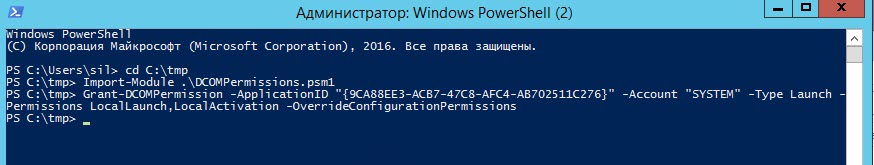
Далее вы можете посмотреть примененные разрешения:
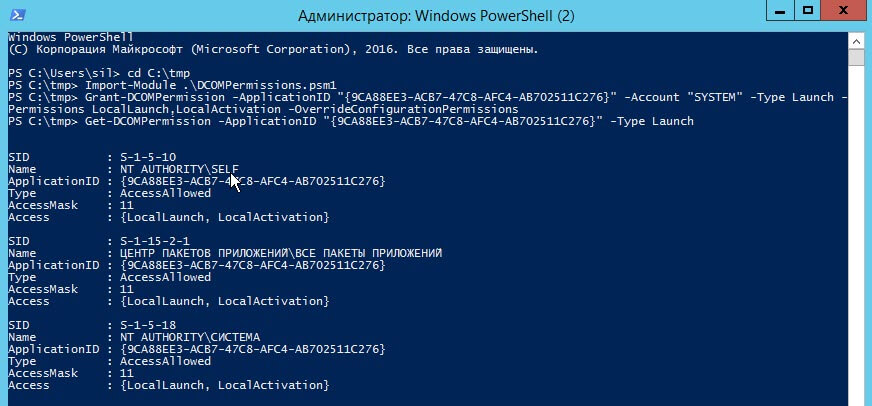
На этом у меня все, мы успешно устранили ошибку DCOM 10016. Я должен подчеркнуть, что ошибка DCOM 10016 вряд ли повлияет на производительность вашей системы. В очень старые времена, когда Microsoft впервые представила «Distributed» в компонентной объектной модели, были уязвимости. Однако эти уязвимости были исправлены, и DCOM теперь безопасен. С вами был Иван Семин, автор и создатель IT портала Pyatilistnik.org.
Development Process
2. Then, we have to use checkAppUpdate function in client like this;
Configuring Login Through the Mini USB Port
You can connect a PC to the mini USB port of a device and then log in to the device to perform basic configurations and management.
V300R019C13 and later versions do not support login through the Mini USB port.
(Optional) Configuring Attributes for the Device Login Through the MiniUSB Port
- Data transmission attributes: transmission rate, flow control mode, parity bit, stop bit, and data bit. These attributes determine the data transmission mode used in the MiniUSB port login process.
- Screen display attributes: timeout period of a connection, number of rows and columns displayed on a terminal screen, and buffer size for historical commands. These attributes determine terminal screen display for MiniUSB port login.
- The system view is displayed.
- Configure data transmission attributes.The data transmission attributes configured on the terminal software must be the same as those on the device.
Run The transmission rate is set.The default transmission rate is 9600 bit/s.
The data bit is set.The default data bit is 8. Data bit configuration depends on the code type used for information interchange. If standard ASCII codes are used, set the data bit to 7. If extended ASCII codes are used, set the data bit to 8.
The parity bit is set.The default parity bit is set to none, indicating that the parity check is not performed on the console port. Setting a parity bit improves data security. If packets on the console port fail to pass the parity check, the device discards the packets.
The stop bit is set.The default stop bit is 1. The stop bit indicates the end of a packet. More stop bits indicate lower transmission efficiency. - Run The transmission rate is set.The default transmission rate is 9600 bit/s.
- The data bit is set.The default data bit is 8. Data bit configuration depends on the code type used for information interchange. If standard ASCII codes are used, set the data bit to 7. If extended ASCII codes are used, set the data bit to 8.
- The parity bit is set.The default parity bit is set to none, indicating that the parity check is not performed on the console port. Setting a parity bit improves data security. If packets on the console port fail to pass the parity check, the device discards the packets.
- The stop bit is set.The default stop bit is 1. The stop bit indicates the end of a packet. More stop bits indicate lower transmission efficiency.
- Configure screen display attributes.If a connection remains idle for the specified timeout period, the system automatically ends the connection after the timeout period expires.The default timeout period is minutes.If you set the timeout period of a terminal connection to 0 or too long, the terminal remains logged in to a device, which is a potential security risk. It is recommended that you run the command to lock the connection.
Run The number of rows displayed on a terminal screen is set.The default number of rows displayed on a terminal screen is 24.The system automatically adjusts the number of terminal screen lines.
Run The number of columns displayed on a terminal screen is set.The default number of columns displayed on a terminal screen is 80. Each character is a column.
Run A buffer size is set for historical commands.The default buffer size is 10, that is, a maximum of 10 historical commands can be buffered. - If a connection remains idle for the specified timeout period, the system automatically ends the connection after the timeout period expires.The default timeout period is minutes.If you set the timeout period of a terminal connection to 0 or too long, the terminal remains logged in to a device, which is a potential security risk. It is recommended that you run the command to lock the connection.
- Run The number of rows displayed on a terminal screen is set.The default number of rows displayed on a terminal screen is 24.The system automatically adjusts the number of terminal screen lines.
- Run The number of columns displayed on a terminal screen is set.The default number of columns displayed on a terminal screen is 80. Each character is a column.
- Run A buffer size is set for historical commands.The default buffer size is 10, that is, a maximum of 10 historical commands can be buffered.
Configuring an Authentication Mode for the Mini USB Interface
- Configure AAA authentication.The system view is displayed.
Run The authentication mode is set to AAA authentication.
(Optional) run An authentication domain is configured.The AAA view is displayed.
Exit the AAA view. - The system view is displayed.
- Run The authentication mode is set to AAA authentication.
- (Optional) run An authentication domain is configured.
- The AAA view is displayed.
- Exit the AAA view.
- Configure password authentication.The system view is displayed.
Run The authentication mode is set to password authentication.
Run set authentication passwordAn authentication password is set. - Run The authentication mode is set to password authentication.
- Run set authentication passwordAn authentication password is set.
Configuring a User Level for the Mini USB Interface
You can connect a PC to the mini USB port of a device and then log in to the device.
- Start the terminal emulation software on the PC. Create a connection, select the connected port, and set communication parameters. (This section uses the third-party software PuTTY as an example.)Click Session to establish a connection, as shown in Figure 10-4. Establishing a connection
Click Serial to set the connected port and communication parameters, as shown in Figure 10-5.Select the connected port based on actual situations. For example, you can view port information in Device Manager in the Windows operating system, and select the connected port.By default, no flow control mode is configured on the device. Because RTS/CTS is selected in the software by default, you need to deselect RTS/CTS; otherwise, you cannot enter commands.If you modify the serial port communication parameters on the device, you must make the same modifications on the PC and then create a connection again. Setting the connected port and communication parameters - Click Session to establish a connection, as shown in Figure 10-4. Establishing a connection
- Click Serial to set the connected port and communication parameters, as shown in Figure 10-5.Select the connected port based on actual situations. For example, you can view port information in Device Manager in the Windows operating system, and select the connected port.By default, no flow control mode is configured on the device. Because RTS/CTS is selected in the software by default, you need to deselect RTS/CTS; otherwise, you cannot enter commands.If you modify the serial port communication parameters on the device, you must make the same modifications on the PC and then create a connection again. Setting the connected port and communication parameters
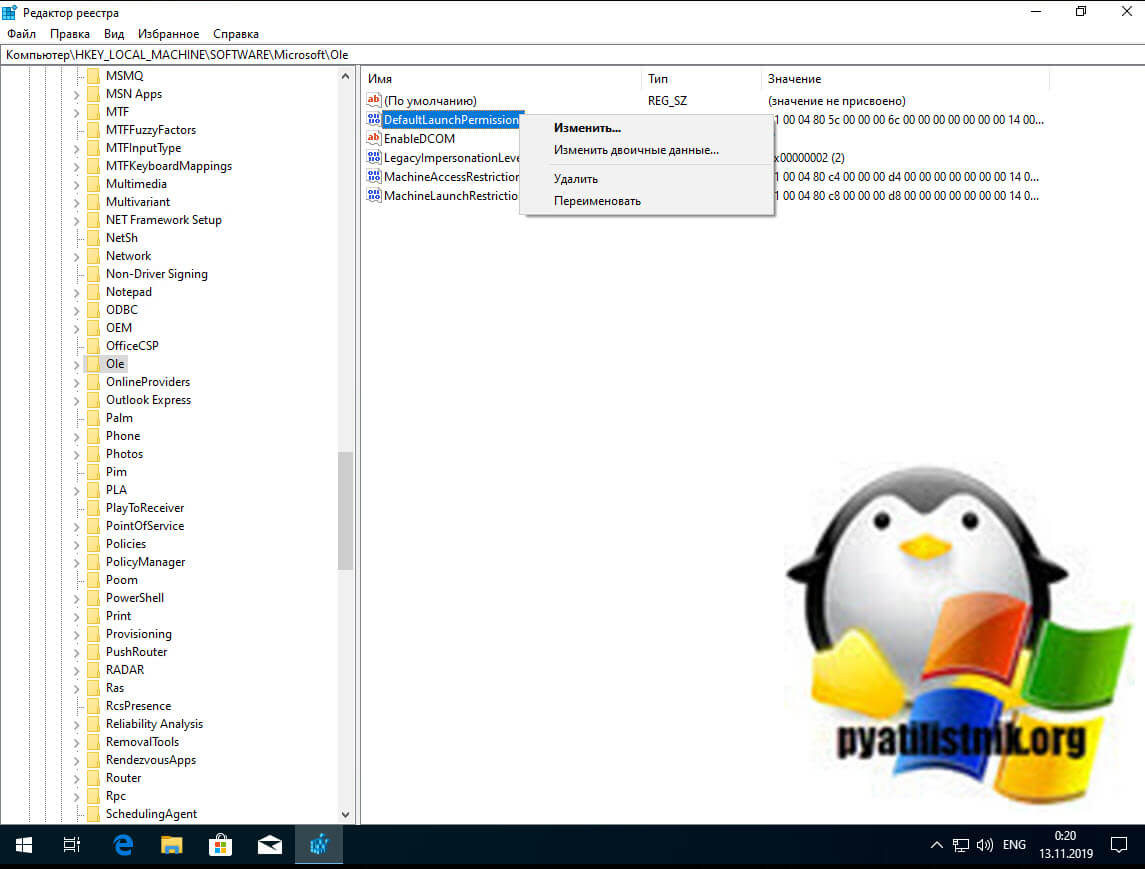
Как исправить ошибку 10016 через удаление ключей из ветки OLe
Данный метод подразумевает удаление нескольких ключей реестра, которые отвечают за проверку прав на COM объекты. Нас будет интересовать ветка реестра:
Ole – эта ветка управляют параметрами запуска по умолчанию и разрешениями доступа, а также возможностями безопасности на уровне вызовов для приложений на основе COM, которые не вызывают CoInitializeSecurity. Только администраторы, создатель объекта и система имеют полный доступ к этой части реестра. Все остальные пользователи имеют доступ только для чтения.
Перед тем, как вы будите вносить изменения я вам советую на всякий случай сделать резервную копию реестра или ветки.
Щелкаем по контейнеру Ole правым кликом и из контекстного меню выберите пункт Экспорт.
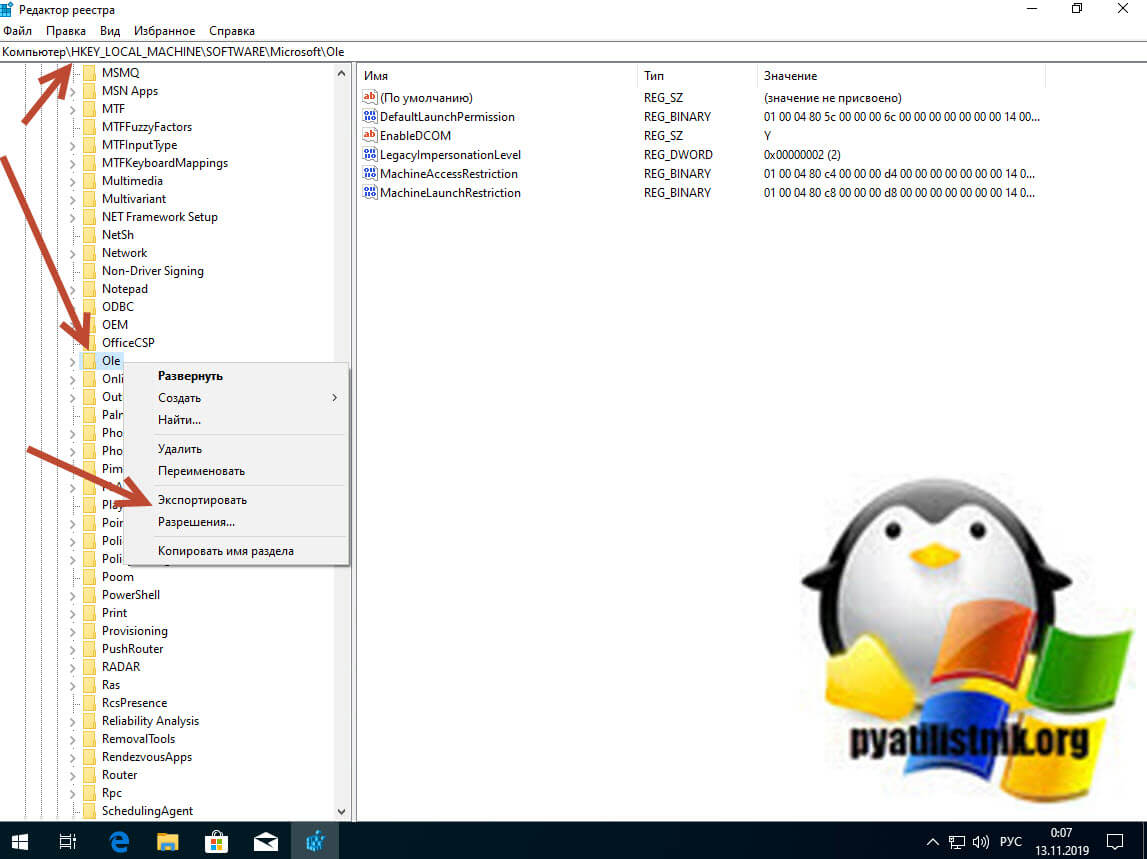
Задаем имя экспортируемого ключа. В случае проблем вы всегда сможете его импортировать и вернуть все к исходному состоянию.
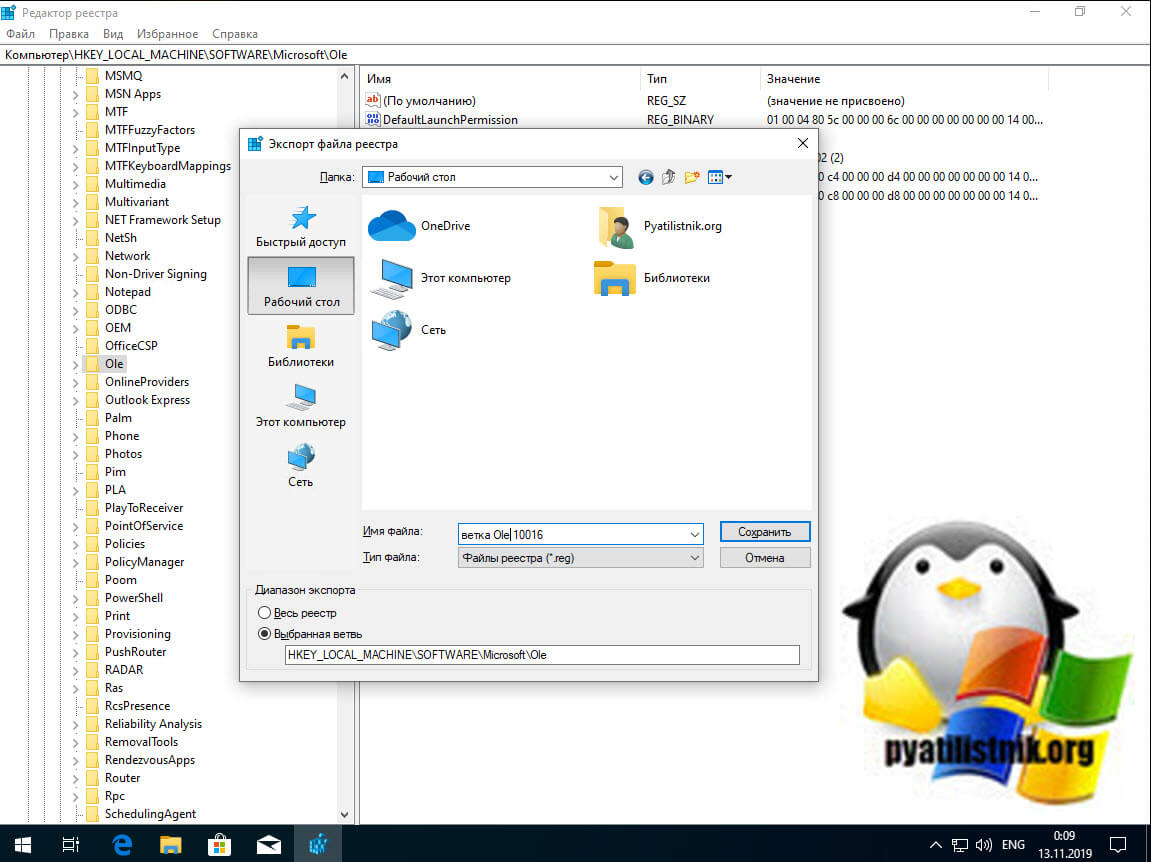
Теперь, чтобы исправить ошибку 10016 в Windows 10 или как у меня в Windows Server 2012 R2 или выше, вам необходимо удалить четыре ключа:
- DefaultAccessPermission – Определяет список разрешений доступа по умолчанию для компьютера. Устанавливает список контроля доступа (ACL) участников, которые могут получить доступ к классам, для которых нет настройки AccessPermission . Этот ACL используется только приложениями, которые не вызывают CoInitializeSecurity и не имеют значения AccessPermission под своим ключом AppID. Среда выполнения COM на сервере проверяет ACL, описываемый этим значением, при олицетворении вызывающей стороны, которая пытается подключиться к объекту, и ее успех определяет, разрешен или запрещен доступ. Если проверка доступа не пройдена, соединение с объектом будет запрещено. Если это именованное значение не существует, только серверу участника и локальной системе разрешается вызывать сервер. По умолчанию это значение не содержит записей. Только принципал сервера и система могут вызывать сервер. Это значение обеспечивает простой уровень централизованного администрирования доступа по умолчанию к подключенным объектам на компьютере.
- DefaultLaunchPermission – Определяет список запуска по умолчанию для компьютера. Определяет список контроля доступа (ACL) участников, которые могут запускать классы, которые не указывают свой собственный ACL через значение реестра LaunchPermission. Права доступа по умолчанию следующие: Администраторы: разрешить запуск, СИСТЕМА: разрешить запуск, ИНТЕРАКТИВНО: разрешить запуск. Если значение LaunchPermission установлено для сервера, оно имеет приоритет над значением DefaultLaunchPermission . После получения локального или удаленного запроса на запуск сервера, у которого ключ AppID не имеет собственного значения LaunchPermission, проверяется ACL, описанный этим значением, при олицетворении клиента, и его успех разрешает или запрещает запуск кода класса.Это значение обеспечивает простой уровень централизованного администрирования запуска по умолчанию для доступа к другим незарегистрированным классам на компьютере. Например, администратор может использовать инструмент DCOMCNFG для настройки системы, чтобы разрешить доступ только для чтения для опытных пользователей. Поэтому OLE будет ограничивать запросы на запуск кода класса членами группы «Опытные пользователи». Впоследствии администратор может настроить разрешения на запуск для отдельных классов, чтобы предоставить возможность запуска кода класса другим группам или отдельным пользователям по мере необходимости.
- MachineAccessRestriction – Устанавливает политику ограничения на уровне компьютера для доступа к компоненту. Принципалы, которым здесь не предоставлены разрешения, не могут получить их, даже если разрешения предоставляются значением реестра DefaultAccessPermission или функцией CoInitializeSecurity. По умолчанию члены группы «Все» могут получать разрешения на локальный и удаленный доступ, а анонимные пользователи могут получать разрешения на локальный доступ.
- MachineLaunchRestriction – Устанавливает политику ограничения на уровне компьютера для запуска и активации компонента. Принципалы, которым здесь не предоставлены разрешения, не могут получить их, даже если разрешения предоставляются значением реестра DefaultAccessPermission или функцией CoInitializeSecurity. По умолчанию администраторы могут получать разрешения на локальный и удаленный запуск и активацию, а члены группы «Все» могут получать разрешения на локальную активацию и запуск.
Подробнее о данной ветке можно почитать по адресу https://docs.microsoft.com/en-us/windows/win32/com/hkey-local-machine-software-microsoft-ole
теперь находим все эти ключи, щелкаем по ним правым кликом мыши и удаляем со спокойной душей, далее я вам советую перезагрузить вашу систему. В подавляющем количестве случаев ошибка с кодом 10016 у вас больше не появится.
Licensing Requirements and Limitations for CLI Login
This section provides licensing requirements and limitations for CLI login.
Involved Network Elements
CLI login configuration is a basic feature of a router and is not under license control.
Hardware Requirements
This section is applicable to all models. For details about differences for specific models, see the description in the corresponding section.


![[VÉLEMÉNY] Huawei Honor 8 Lite (#2019) – Műszaki adatok és vélemények!](https://huaweidevices.ru/wp-content/uploads/2020/08/Huawei-Honor-8-1-630x420-150x150.jpg)





